What Are Piggybacking Tags and What Threats Do They Pose?

Piggybacking tags can pose a threat to the privacy and security of your website data—but the threat is preventable if you’re willing to take the right course of action.
But first, let’s give a face to our potential adversary.
What Is a Piggybacking Tag?
Piggybacking tags are data collection technologies loaded onto a site by another tag (often called a container tag). Tags are those snippets of code your analytics, advertising, and other MarTech vendors have you install on your site, so they can collect the data they need to operate.
One form of container tag you’re probably familiar with is the TMS container snippet. While not usually considered in the context of tag piggybacking, in reality your tag management’s container snippet deploys piggybacking tags. Any tag that acts as a container for other tags uses piggybacking.
Piggybacking tags are most prevalent in the ad-serving community as a way for one ad server’s tag to initiate tags from other servers—allowing multiple tags to collect data without having to implement each individually.
So in reality, piggybacking is common and can be quite useful, when used appropriately. But when mishandled, it can get out of control.
What Dangers Do Piggybacking Tags Pose?
Piggybacking tags can become dangerous because software employed for privacy compliance, like Consent Management Platforms and Tag Management Systems, have difficulty seeing them. This can compromise your compliance efforts and allow third parties to gain access to your website data. Piggybacking tags can also reduce your website’s performance.
These negative consequences can snowball: one vendor deploys a container, which deploys another container, and so on. As piggybacking tags daisy-chain downward with more and more tags, the following threats increase in likelihood:
Data leakage. Data leakage is the transmission of website data to an unauthorized party. As more and more tags appear on your site, more parties have access to your data, increasing the likelihood that your data could fall into the wrong hands.
Non-compliance. Especially in the wake of GDPR, CCPA, LGDP and other data protection regulation, making sure that data collection complies with both internal and external controls is essential. Non-compliant data collection, tags, and cookies are more likely to happen if your website is heavy on piggybacking.
Slow load times. Each piggybacking tag means an additional request to a server somewhere, increasing the load on your visitor’s connection and constricting bandwidth. The result: a slow website. Not ideal.
Data loss. Related to slow website load times, if your tags can’t load fast enough due to blocking piggybacking tags, you risk losing customer data.
Some Ways to Detect Tag Piggybacking
Again, not all piggybacking is bad. Still, piggybacking is worrisome mainly because of the hidden nature of it. How can you really know if piggybacking is a problem on your site?
Below are some techniques and tools you can use to identify piggybacking and other unauthorized tags on your site.
Using your browser’s developer tools or a proxy tool
The way most website stakeholders will identify piggybacking & rogue tags on their site is using the developer tools in their browser. The Network tab in the developer tools allows you to see all network requests coming in and out of your browser, including those made by tags on your site. The network requests look something like this:
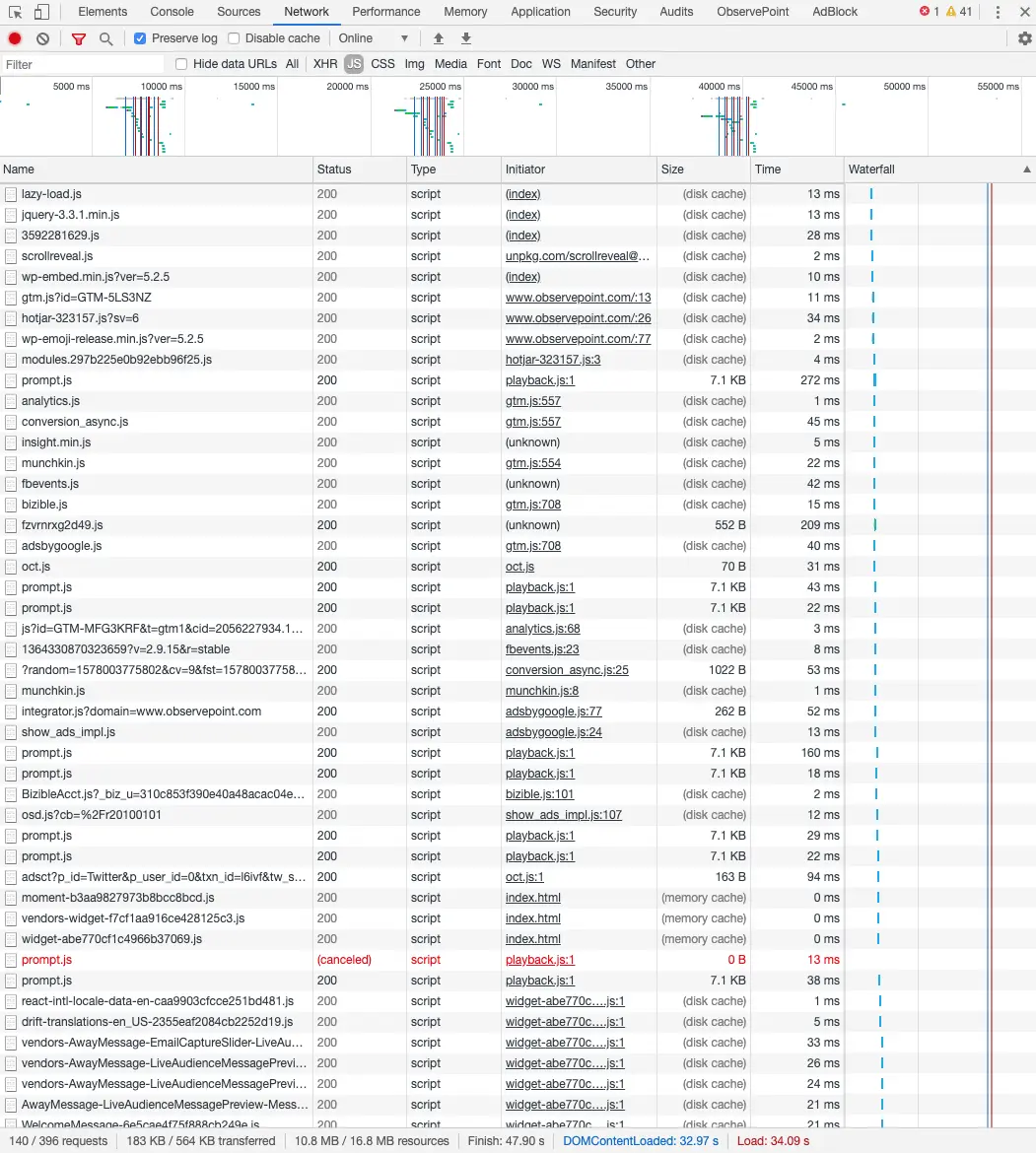
Each line in the table represents a request for a resource (in this case, JavaScript files). You would see a similar list of requests if you were using a proxy tool like Charles or Fiddler.
Good
The good thing about the report in the browser’s developer tools (or a proxy tool) is that the report is comprehensive: it contains every single request for any resource, including the initial requests for a given vendor’s script and subsequent image/XHR requests made by those scripts. So if there’s something loading on your page, you will be able to see it in the developer tools.
Bad
As you can see, the list of requests in the developer tools isn’t very human-friendly. You have to really know what you’re looking for. The problem is, when you’re looking for piggybacking tags, you don’t know what you’re looking for, so you’ll have a grand old time combing through all the requests to find something that may or may not be there.
On another note, you’ll only find unauthorized scripts when you look for them—and you have much better things to do than spend all your time searching for unauthorized tags.
Using a tag debugger
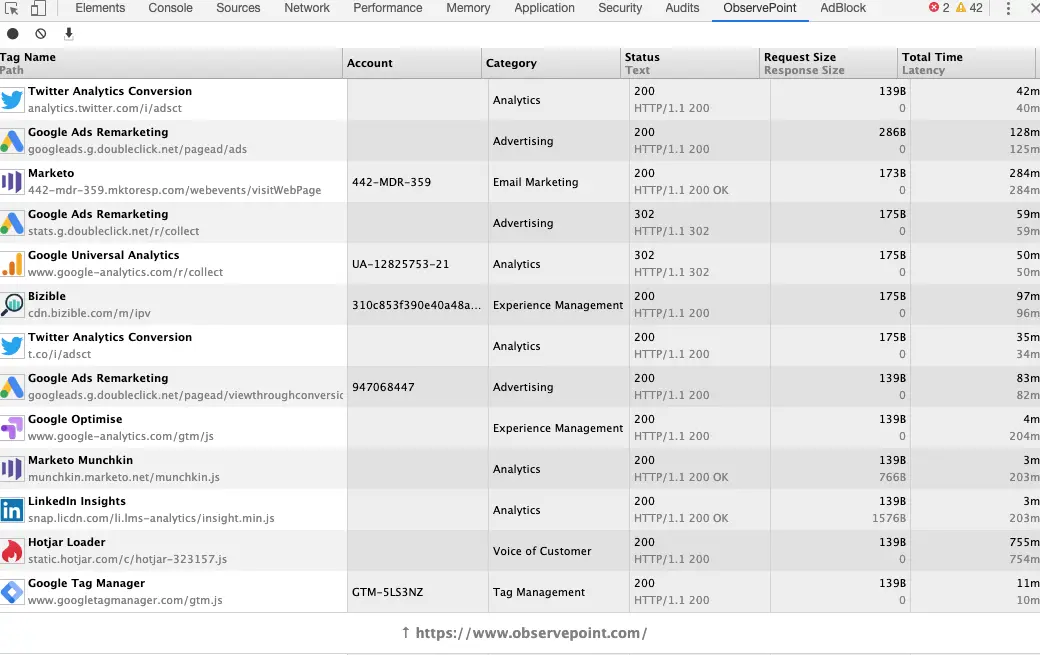
Another alternative is to use a tag debugger. One option is, drum roll, ObservePoint’s TagDebugger. The TagDebugger is an alternative to the Network tab, making those network requests more human-friendly:
Good
ObservePoint’s TagDebugger is a free Chrome Extension and is a great place to start when you need to identify what tags you have on your site. The TagDebugger identifies which tags are on your site based on the unique signature of the requests, allowing you to detect piggybacking tags that ObservePoint recognizes.
Bad
One of the limitations of the TagDebugger is that you won’t be able to see how tags arrived on your site. For example, say you used the debugger and identified a stray ad tag that shouldn’t be there. How did it get there? You’ll have to uncover that answer for yourself.
In addition, it’s impossible for the TagDebugger to recognize and categorize every single request on any website. The TagDebugger only recognizes a specific list of vendors, so if a rogue script with an unrecognized signature is piggybacking off one of your other tags, the TagDebugger won’t recognize it.
Setting up monitoring for any and all rogue & piggybacking tags
The optimal solution for mitigating the risk of rogue & piggybacking tags would be able to:
- Identify any unauthorized request, regardless of its signature
- Conduct continuous monitoring to alert you in near real-time as an unauthorized request appears
- Easily identify the source of the unauthorized request
ObservePoint’s Privacy Compliance solution answers each of these requirements. Here’s how it works:
- ObservePoint runs a scan to identify all requests coming off your site, then exports the list and shares it with you.
- You, the website stakeholder, identify which request domains are authorized, creating a whitelist of approved domains.
- ObservePoint uploads the whitelist into their system, setting up alerts for whenever a request appears that does not match one of the approved domains.
A feature of the Privacy Compliance solution called Tag Initiators shows you the relationship between data collection technologies and cookies in an easy-to-read, visual map. It can drastically simplify the process of discovering tags and seeing how they arrived on your site, allowing you to easily identify which tags are the source of piggybacking. Once you know the source, you can either remove it or lean on your vendors to tighten up their piggybacking practices.
And voilà, there you have it. Once you’ve set up monitoring, you can rest easy knowing that whenever a tag appears whose signature doesn’t match one of your approved domains, you will receive an alert immediately.
Protecting Your Site from Unauthorized Data Collection
The most common way data breaches occur is through a vulnerability in a third-party vendor. Don’t let your vendors be a vulnerability to you. Make sure to set up proper governance to ensure no unauthorized tags appear on your site.
ObservePoint can help you stop worrying about piggybacking tags. To learn more, schedule a demo of the Privacy Compliance solution.